windows xp上的通用shellcode
开发环境
windows xp sp3
visual C++ 6.0
shellcode适用环境
windows xp sp3及之前版本,windows 7稍微改动亦可
1.获取3个函数名hash后的值
通过将字符串进行hash计算,得到一个更短的字符串,从而简化shellcode中字符串对比的代码。
hash函数的C代码如下:
|
|
得到hash值为:
MessageBoxA : 0x1e380a6a
ExitProcess : 0x4fd18963
LoadLibraryA : 0x0c917432
2.编写shellcode
首先将3个函数的hash值压入栈
|
|
然后抬高栈,保护shellcode不被入栈数据破坏
|
|
将“use32“字符串压入栈,后面LoadLibraryA调用时需要该参数
|
|
此时栈中的状态如图所示: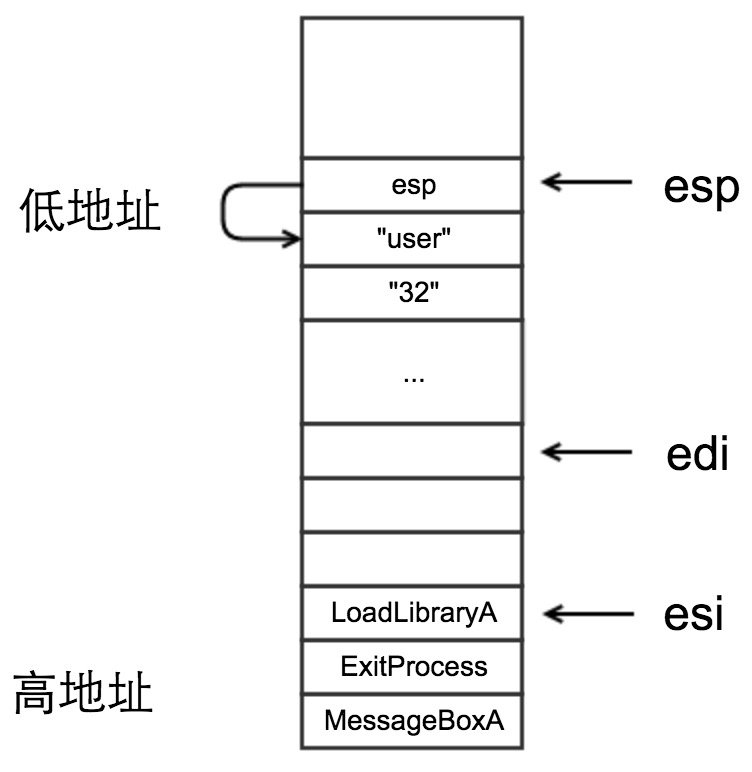
找到kernel32.dll的基址
|
|
开始查找3个函数的地址
|
|
这3个函数的查找方法:
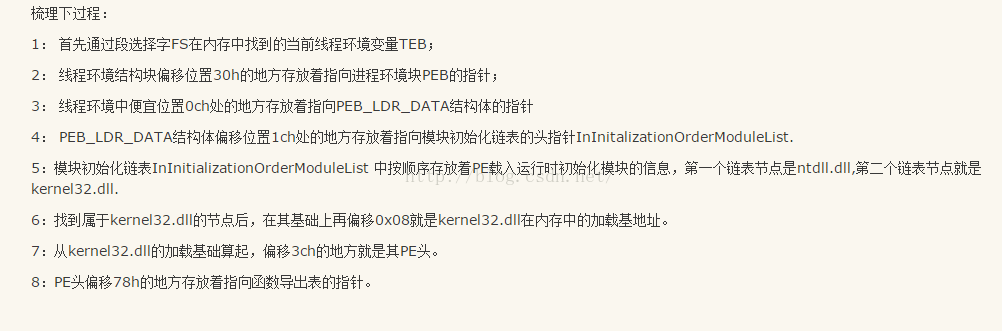
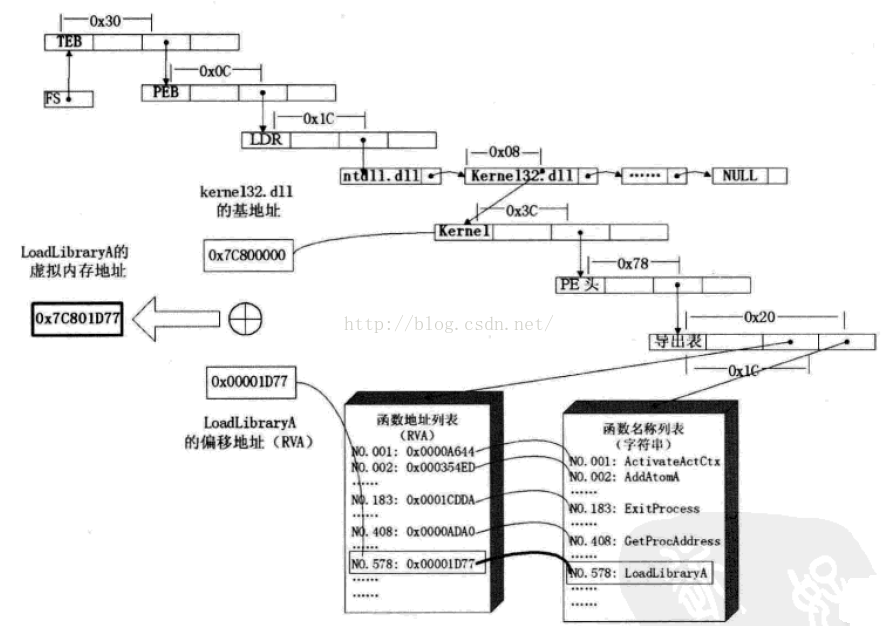
查找kernel32.dll地址,以及从kernel32.dll中查找LoadLibraryA函数过程:
函数查找顺序
[1]. LoadLibraryA -> ExitProcess -> MessageBox
[2]. 找到的各函数地址,依次存储在前面栈图中的edi所指向的空间;
[3]. 每次查找时,将ebp指向相应函数所在的dll地址;
[4]. 最后找MessageBox,在找MessageBox之前,调用LoadLibraryA函数,加载user32,并将ebp指向user32首地址;
3. 整体代码如下
|
|
编译查看exe文件,提取shellcode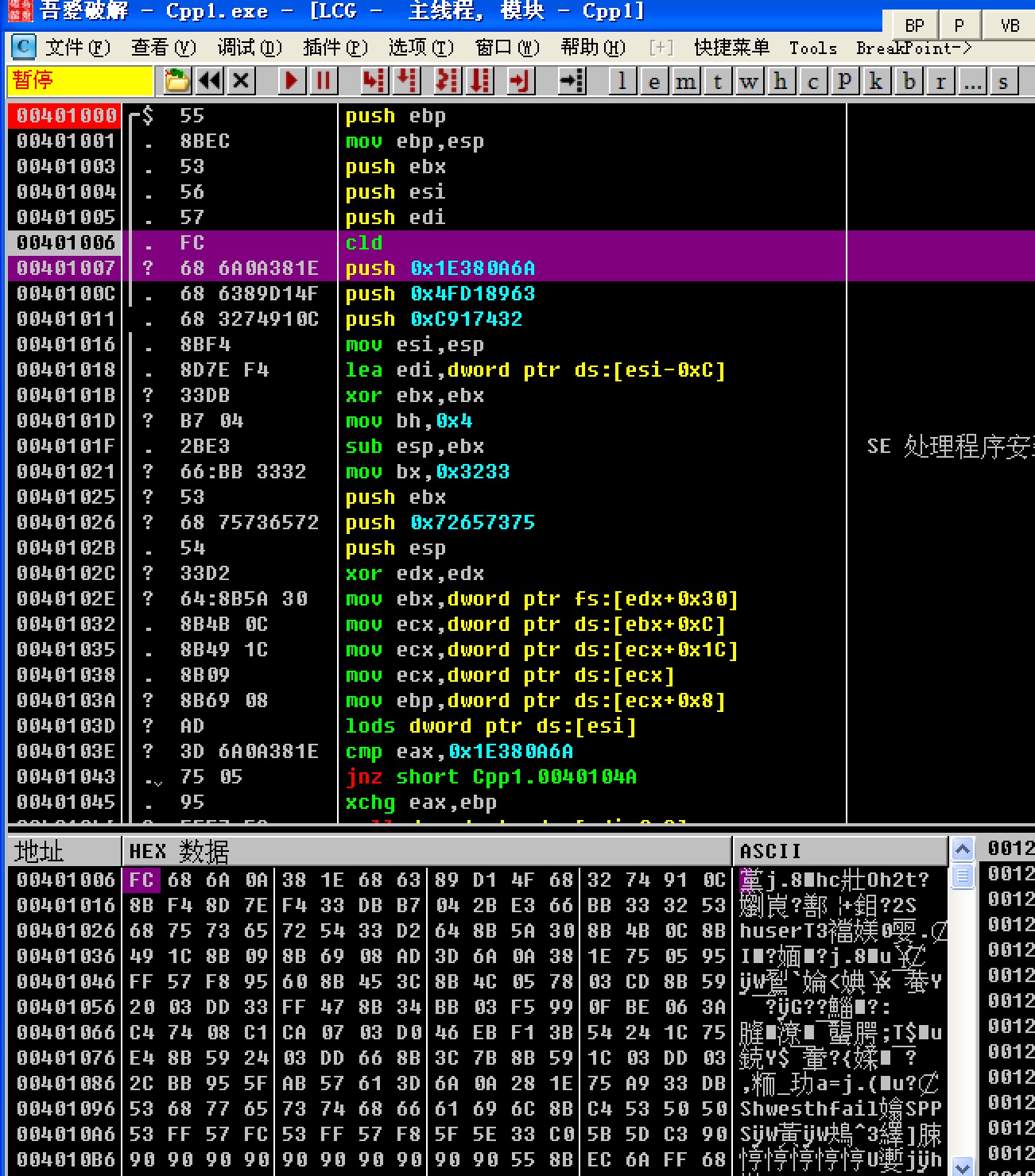
|
|